Background
This document provides an overview of integrating IBM Cloud Secret Manager with the External Secret Operator. It outlines the benefits of using these tools together, the setup process, and how to manage secrets effectively in a Kubernetes environment. By leveraging IBM Cloud Secret Manager alongside the External Secret Operator, users can enhance their security posture while simplifying secret management in cloud-native applications.
Introduction
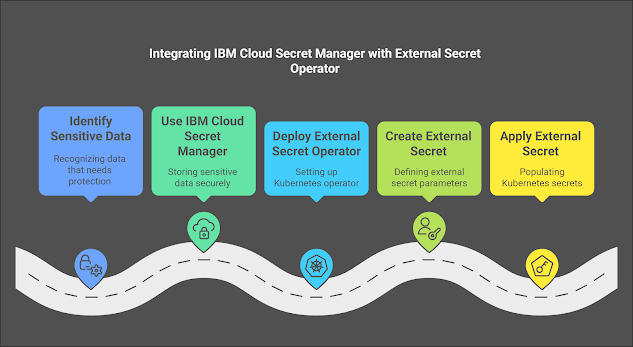
IBM Cloud Secret Manager is a secure service for managing sensitive information such as API keys, passwords, and certificates. The External Secret Operator is a Kubernetes operator that allows you to use external secret management systems to populate Kubernetes secrets. By combining these two powerful tools, organizations can streamline their secret management processes while ensuring that sensitive data is securely stored and accessed.
Benefits of Using IBM Cloud Secret Manager with External Secret Operator
Enhanced Security: Secrets are stored securely in IBM Cloud Secret Manager, reducing the risk of exposure.
Centralized Management: Manage all secrets from a single location, simplifying operations and compliance.
Dynamic Secrets: Automatically update Kubernetes secrets when the IBM Cloud Secret Manager changes occur.
Kubernetes Native: Seamlessly integrates with Kubernetes, allowing developers to work within familiar environments.
Prerequisites
Before proceeding with the setup, ensure you have the following:
An IBM Cloud account with access to IBM Cloud Secret Manager.
A Kubernetes cluster where you can deploy the External Secret Operator.
kubectlcommand-line tool installed and configured to interact with your Kubernetes cluster.
Source: https://cloud.ibm.com/docs/secrets-manager?topic=secrets-manager-tutorial-kubernetes-secrets
Login to IBM Cloud Console:
Search for Secret manager
Provision Secret manager
Setup Instructions
Step 1: Install the External Secret Operator
To install the External Secret Operator, you can use Helm. First, add the Helm repository:
helm repo add external-secrets https://charts.external-secrets.io
helm install external-secrets external-secrets/external-secrets \
-n external-secrets \
--create-namespace \
--set installCRDs=trueStep 2: Configure IBM Cloud Secret Manager
Create a Secret: Log in to your IBM Cloud account and navigate to the Secret Manager service. Create a new secret and note its name and ID.IAM API Key: Create an IAM API key with permissions to access the Secret Manager.
Step 3: Create a Kubernetes Secret for the IAM API Key
Store the IAM API key in a Kubernetes secret:
kubectl create secret generic ibm-cloud-secret-manager --from-literal=api-key='<YOUR_IAM_API_KEY>'
Step 4: Define an External Secret
Create a YAML file for the External Secret that references the IBM Cloud Secret Manager. Here’s an example:
apiVersion: external-secrets.io/v1beta1
kind: ExternalSecret
metadata:
name: my-secret
spec:
backendType: ibmcloud
data:
- key: <YOUR_SECRET_NAME>
name: <K8S_SECRET_KEY_NAME>
refreshInterval: 1h
serviceAccount: <YOUR_SERVICE_ACCOUNT>
Replace <YOUR_SECRET_NAME> and <K8S_SECRET_KEY_NAME> with your actual secret name and desired Kubernetes secret key name.
Step 5: Apply the External Secret
Deploy the External Secret to your Kubernetes cluster:
kubectl apply -f external-secret.yaml
Managing Secrets
Once the External Secret is set up, the External Secret Operator will automatically sync the secrets from IBM Cloud Secret Manager to your Kubernetes cluster. You can manage your secrets directly from the IBM Cloud console, and any updates will be reflected in your Kubernetes environment based on the defined refresh interval.
Conclusion
Integrating IBM Cloud Secret Manager with the External Secret Operator provides a robust solution for managing secrets in Kubernetes. This setup not only enhances security but also simplifies the management of sensitive data across cloud-native applications. By following the outlined steps, organizations can ensure that their secrets are securely stored and efficiently accessed, paving the way for more secure application development and deployment.

.png)
.png)
.png)




.png)
.png)
.png)

.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)
.png)
